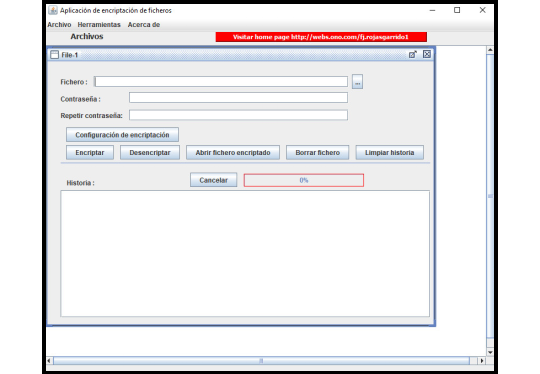
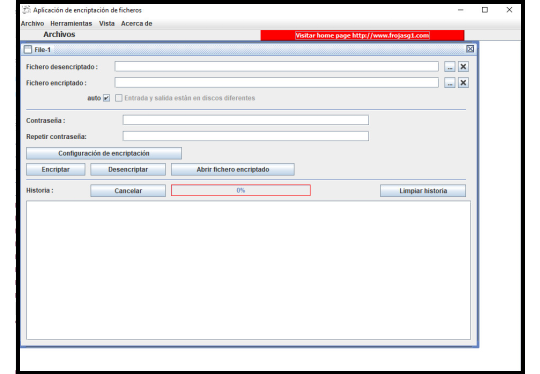
For the development of this application, a proprietary encryption method has been implemented:
- Based on XOR stream encryption.
- Chaotic pseudo-random generator.
- Passwords for the pseudo-random generator can be up to 16,000 bits long.
- The number of possible combinations is limited by the password's strength, which uses a 32-byte hash.
- The user can modify the settings to enable byte reordering during encryption, significantly slowing down brute-force attacks.
- The user can cancel the encryption or decryption process at any time.
It is built on the platform library v1.4, which includes many common features across all applications
With version 1.7, the computation time required to break brute-force encryption is greatly increased, without increasing the decryption time experienced by the user.
The type of encryption used in this application relies on a pseudo-random bit stream, which is used for character reordering and then for encryption/decryption using the XOR mask method. This is done in slices.
The increase in the time required to break the encryption by brute force is achieved by making it absolutely necessary for the first slice to be completely reordered before proceeding with the decryption of the characters with the XOR.
And this is achieved by making the XOR encryption/decryption use the same pseudo-random generator used in the reordering process, starting the XOR phase from the state of the generator just after the reordering.
This way, there are no possible shortcuts to trying to decrypt by brute force.